Flow data diagram security level dfd system visit yc examples network Use case of home security system Diagram security thms transformer monitoring implementation gsm data flow diagram for home security system
Program flow chart of the proposed home security system. | Download
Home security system Your guide to fedramp diagrams Program flow chart of the proposed home security system.
Security network diagram control computer diagrams devices networks secure access encryption solution cloud examples model architecture example conceptdraw software system
Data flow diagramData flow: creating a bbm enterprise conference Data flow home security system ppt powerpoint presentation infographicPremium vector.
Microsoft graph security api data flowBlock diagram of home security system Data flow diagram of smart security frameworkData management process flow diagram.

Gsm based microcontroller proposed
(pdf) design and development of home security systems based on internetMicrocontroller based home security system with gsm technology B. schematic diagram of home security system with sensor(s)Smart iot system based automation diagram security er implementation flowchart flow data ermodelexample atlantis press.
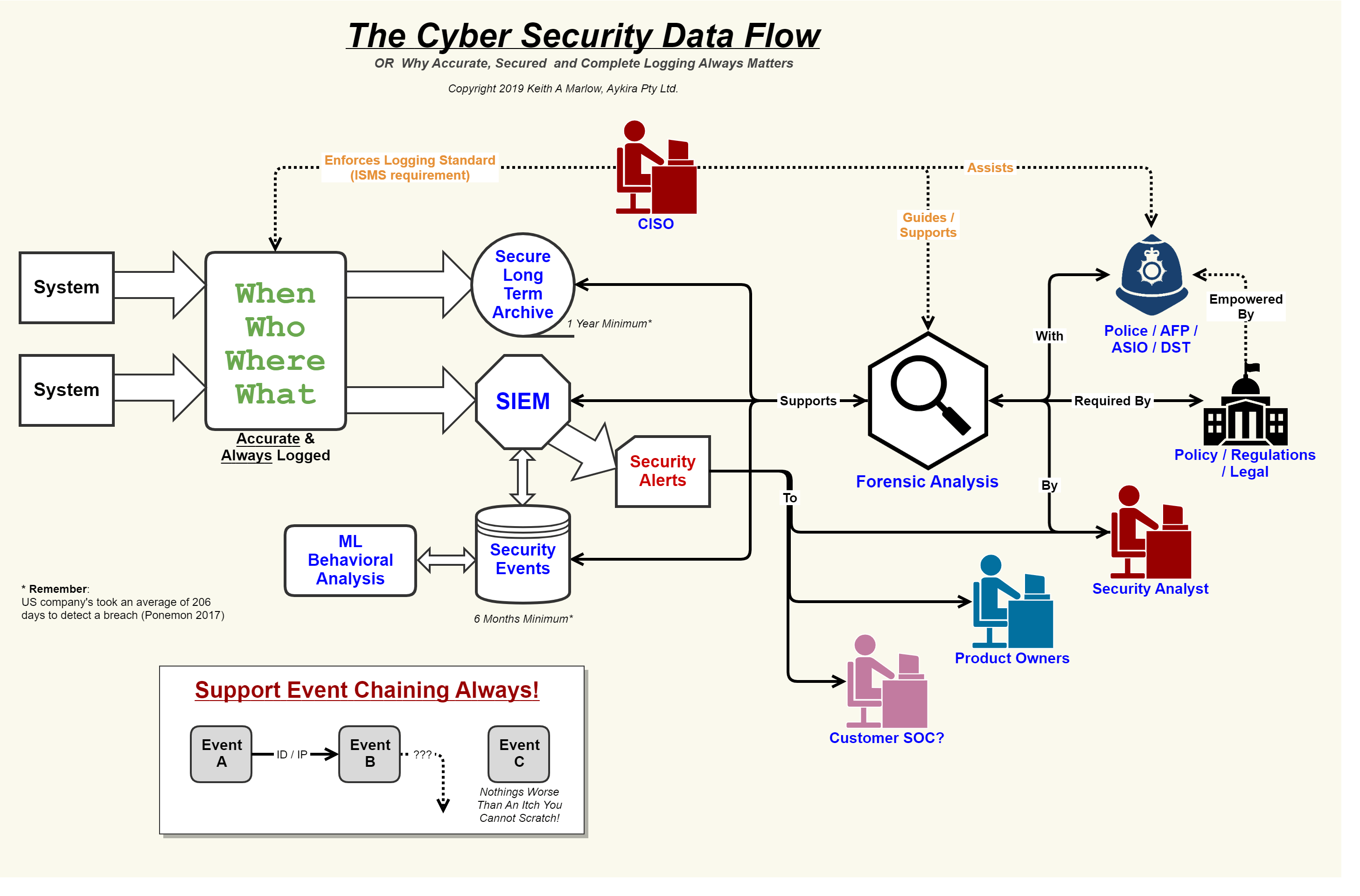
Application map diagramLibreoffice draw network diagram template Security flow data cyber event logging diagram internet logs important why so together showing concerning events au puttingSystem entity semantics notations.

Lecture 13 requirements modeling
Flowchart system chartHome security appliances flowchart Home security system flowchart with electronic key and lock remoteData flow diagram in software engineering.
Security camera wiring diagram schematicData flow and security overview The following data flow diagram template highlights data flows in aSecurity system.

Architecture diagram of home security system
Home security system: er diagram for home security systemNetwork security model Demo startSecurity event logging, why it is so important – aykira internet solutions.
Data flow diagramHome security system [cs open courseware] Er diagram for home automation system – ermodelexample.comSchematic diagram of the proposed home security system.